Single Sign-On and Active Directory Integration
Command 360 supports any SAML2-based authentication single sign-on (SSO) and active directory (AD) integration. This is configured during system installation while setting up a Third-Party Identity Provider (IdP).
Note
In the context of SAML endpoints, all URLs are case-sensitive.
If you are using Microsoft Entra ID SSO, see Configuring SSO with Microsoft Entra ID for a tutorial on setting this up with Command 360.
SAML Certificate Generation
Before configuring Third-Party IdP settings, the admin of the SSO system needs to create an SAML application, then generate an SSO signing certificate. Use the following values when generating the certificate:
Assertion Consumer Service URL:
https://<FQDN of the Command 360 Manager>/Haivision/Authorization/Saml2/AcsAudience:
https://haivision/external/identity
Third-Party System & Admin Settings
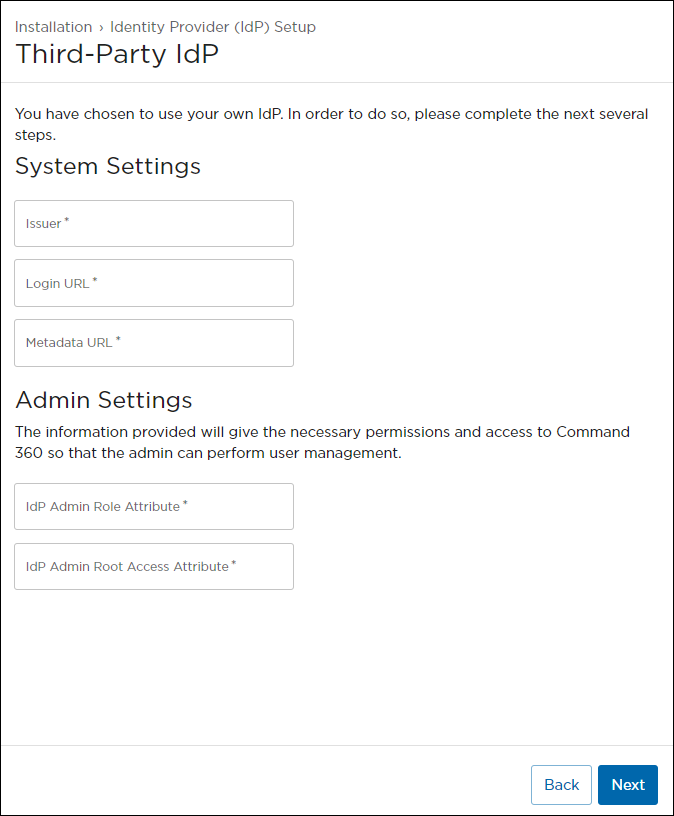
Third-Party IdP Setup Screen
The following fields from the generated SAML certificate are necessary to complete SSO setup on Command 360:
Setting | Description | Example |
|---|---|---|
System Settings | ||
Issuer | The Entity ID of your IdP. This is a URL that uniquely identifies your IdP. |
|
Login URL | The SAML service provider URL the user signs in to. |
|
Metadata URL | The URL for the service provider from which user metadata is sent. |
|
Admin Settings | ||
IdP Admin Role Attribute | An attribute from your SAML token that identifies a user that should be granted the Command 360 admin role for initial setup. This maps to the Hai_Admin XREF value (see Roles and Permissions). |
|
IdP Admin Root Access Attribute | An attribute from your SAML token that identifies a user that should be granted the Command 360 admin access group for initial setup. This maps to the Hai_Root XREF value (see Access Groups). |
|
